Microsoft on Tuesday released 89 patches affecting 14 product families. Two of the addressed issues, both touching Windows, are considered by Microsoft to be of critical severity. At patch time, two of the issues addressed are known to be under exploit in the wild, with eight additional CVEs more likely to be exploited in the next 30 days by the company’s estimation. Four of this month’s issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on two Edge-related CVEs, and one related to Azure, CBL Mariner, and Defender (more on that advisory below). We are as always including at the end of this post additional appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total CVEs: 89
- Publicly disclosed: 3
- Exploit detected: 2
- Severity
- Critical: 3
- Important: 85
- Moderate: 3
- Impact
- Remote Code Execution: 52
- Elevation of Privilege: 27
- Denial of Service: 4
- Spoofing: 3
- Security Feature Bypass: 2
- Information Disclosure: 1
- CVSS base score 9.0 or greater: 4
- CVSS base score 8.0 or greater: 42
Figure 1: RCE vulnerabilities, bolstered by a strong showing among the 31 SQL Server issues patched, constitute the majority of November’s updates
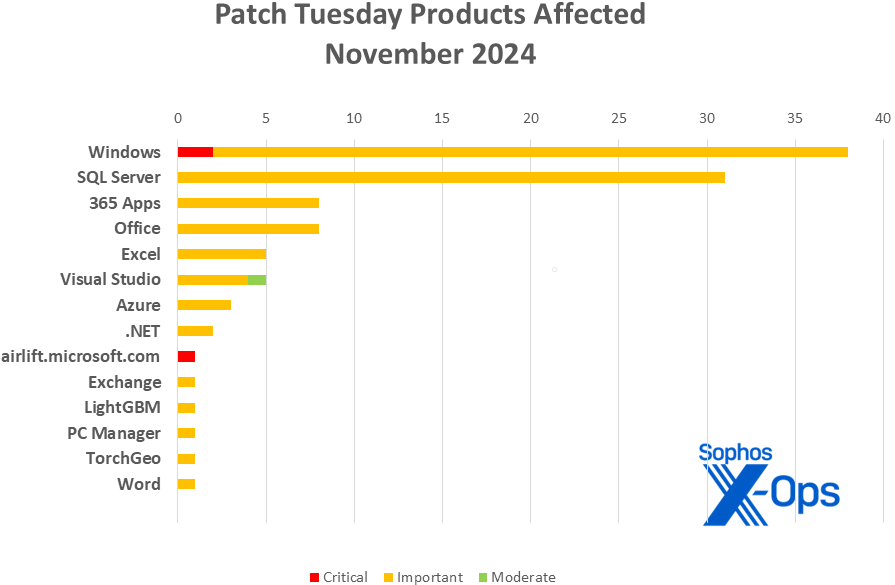
Products
- Windows: 37
- SQL Server: 31
- 365 Apps: 8
- Office: 8
- Excel: 5
- Visual Studio: 5
- Azure: 3
- .NET: 2
- airlift.microsoft.com: 1
- Exchange: 1
- LightGBM: 1
- PC Manager: 1
- TorchGeo: 1
- Word: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect.
Figure 2: The variety of affected product families rivals last month’s, but Windows and SQL Server took the vast majority of November’s patches
Notable November updates
In addition to the issues discussed above, a number of specific items merit attention.
31 CVEs – Server 2025 issues
As reported in The Register last week, a KB error led to quite a number of instances of Server 2019 and 2022 receiving surprise upgrades to Server 2025. Though Microsoft eventually acknowledged and worked to mitigate the problem, as of this writing that process appears to still be underway. Meanwhile, this month’s Patch Tuesday’s set gives administrators one more very good reason to prioritize sorting out any unexpected Server 2025 presence on their systems, as over a third of the month’s patches affect the not-yet-official new version. We have listed those CVEs in Appendix E at the end of this writeup.
CVE-2024-5535 — OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread
It’s relegated to the list of advisories, but this RCE, which carries a hefty 9.1 CVSS base score, merits a look. The information available is also noteworthy (though, as an OpenSSL-assigned CVE, it’s slightly different to the usual data Microsoft presents on its patches) – the available information advises that, in a worst-case scenario of attack via email, RCE could be achieved even if the user does not open, read, or click on a received link. The issue affects version 3.0 of Azure Linux, version 2.0 of CBL Mariner, and Defender for Endpoint on Android, iOS, and Windows. That said, Microsoft judges it less likely to be exploited in the next 30 days.
CVE-2024-49039 — Windows Task Scheduler Elevation of Privilege Vulnerability
CVE-2024-43451 — NTLM Hash Disclosure Spoofing Vulnerability
These are the two CVEs that Microsoft has found to be already under exploit in the wild. The first is the more serious of the two – an EoP with a CVSS base score of 8.8. Both require that the target system run a malicious application. The spoofing issue, which weighs in at a relatively less alarming 6.5 CVSS base, includes an additional surprise – IE Cumulative updates for users of Server 2008, 2008 R2, and 2012 R2 still taking Security Only updates.
CVE-2024-49040 — Microsoft Exchange Server Spoofing Vulnerability
This Important-severity spoofing vulnerability, which Microsoft believes to be more likely to be exploited within the next 30 days, has a rather specific set of post-installation instructions, which can be seen on the company’s site.
CVE-2024-49056 — airlift.microsoft.com Elevation of Privilege Vulnerability
An unusual CVE against a Microsoft micro-site, this Critical-severity EoP has already been patched. According to the information provided, “Authentication bypass by assumed-immutable data on airlift.microsoft.com allow[ed] an authorized attacker to elevate privileges over a network.”
Figure 3: With a month left to go in the year, and after remarkably low CVE counts in the first three months, 2024 has now officially exceeded the patch count for all of last year – 942 patches so far in 2024, as opposed to 931 for all of 2023
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-43623 | Exp/2443623-A | Exp/2443623-A |
| CVE-2024-43630 | Exp/2443630-A | Exp/2443630-A |
| CVE-2024-49039 | Exp/2449039-A | Exp/2449039-A |
| CVE-2024-49033 | sid:2310318 | sid:2310318 |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of November patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (52 CVEs)
| Critical severity | |
| CVE-2024-43639 | Windows Kerberos Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-38255 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43447 | Windows SMBv3 Server Remote Code Execution Vulnerability |
| CVE-2024-43459 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43462 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-43598 | LightGBM Remote Code Execution Vulnerability |
| CVE-2024-43602 | Azure CycleCloud Remote Code Execution Vulnerability |
| CVE-2024-43620 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43621 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43622 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43627 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43628 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43635 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43640 | Windows Kernel-Mode Driver Remote Code Execution Vulnerability |
| CVE-2024-48993 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48994 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48995 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48996 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48997 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48998 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48999 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49000 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49001 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49002 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49003 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49004 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49005 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49006 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49007 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49008 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49009 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49010 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49011 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49012 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49013 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49014 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49015 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49016 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49017 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49018 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49021 | Microsoft SQL Server Remote Code Execution Vulnerability |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Remote Code Execution Vulnerability |
| CVE-2024-49048 | TorchGeo Remote Code Execution Vulnerability |
| CVE-2024-49050 | Visual Studio Code Python Extension Remote Code Execution Vulnerability |
Elevation of Privilege (27 CVEs)
| Critical severity | |
| CVE-2024-43625 | Microsoft Windows VMSwitch Elevation of Privilege Vulnerability |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2024-43449 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43452 | Windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43530 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-43613 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43624 | Windows Hyper-V Shared Virtual Disk Elevation of Privilege Vulnerability |
| CVE-2024-43626 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43631 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43634 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43637 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43638 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43641 | Windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43643 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43644 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2024-43646 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49042 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-49044 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-49046 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-49051 | Microsoft PC Manager Elevation of Privilege Vulnerability |
| Moderate severity | |
| CVE-2024-49049 | Visual Studio Code Remote Extension Elevation of Privilege Vulnerability |
Denial of Service (4 CVEs)
| Important severity | |
| CVE-2024-38264 | Microsoft Virtual Hard Disk (VHDX) Denial of Service Vulnerability |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43633 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43642 | Windows SMB Denial of Service Vulnerability |
Spoofing (3 CVEs)
| Important severity | |
| CVE-2024-43450 | Windows DNS Spoofing Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2024-49040 | Microsoft Exchange Server Spoofing Vulnerability |
Security Feature Bypass (2 CVEs)
| Important severity | |
| CVE-2024-43645 | Windows Defender Application Control (WDAC) Security Feature Bypass Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability |
Information Disclosure (1 CVE)
| Important severity | |
| CVE-2024-43500 | Windows Resilient File System (ReFS) Information Disclosure Vulnerability |
Appendix B: Exploitability
This is a list of the November CVEs judged by Microsoft to be either under exploitation in the wild or more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation detected | |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Privilege Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43642 | Windows SMB Denial of Service Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability |
| CVE-2024-49040 | Microsoft Exchange Server Spoofing Vulnerability |
Appendix C: Products Affected
This is a list of November’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (37 CVEs)
| Critical severity | |
| CVE-2024-43625 | Microsoft Windows VMSwitch Elevation of Privilege Vulnerability |
| CVE-2024-43639 | Windows Kerberos Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-38203 | Windows Package Library Manager Information Disclosure Vulnerability |
| CVE-2024-38264 | Microsoft Virtual Hard Disk (VHDX) Denial of Service Vulnerability |
| CVE-2024-43447 | Windows SMBv3 Server Remote Code Execution Vulnerability |
| CVE-2024-43449 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43450 | Windows DNS Spoofing Vulnerability |
| CVE-2024-43452 | Windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43530 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-43620 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43621 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43622 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43623 | Windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43624 | Windows Hyper-V Shared Virtual Disk Elevation of Privilege Vulnerability |
| CVE-2024-43626 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-43627 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43628 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43629 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43631 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43633 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43634 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43635 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43637 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43638 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43640 | Windows Kernel-Mode Driver Remote Code Execution Vulnerability |
| CVE-2024-43641 | Windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43642 | Windows SMB Denial of Service Vulnerability |
| CVE-2024-43643 | Windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43644 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2024-43645 | Windows Defender Application Control (WDAC) Security Feature Bypass Vulnerability |
| CVE-2024-43646 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-49019 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| CVE-2024-49039 | Windows Task Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49046 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
SQL Server (31 CVEs)
| Important severity | |
| CVE-2024-38255 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43459 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-43462 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48993 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48994 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48995 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48996 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48997 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48998 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-48999 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49000 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49001 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49002 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49003 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49004 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49005 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49006 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49007 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49008 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49009 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49010 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49011 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49012 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49013 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49014 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49015 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49016 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49017 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49018 | SQL Server Native Client Remote Code Execution Vulnerability |
| CVE-2024-49021 | Microsoft SQL Server Remote Code Execution Vulnerability |
| CVE-2024-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Remote Code Execution Vulnerability |
365 Apps (8 CVEs)
| Important severity | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability |
Office (8 CVEs)
| Important severity | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability |
Excel (5 CVEs)
| Important severity | |
| CVE-2024-49026 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Remote Code Execution Vulnerability |
Visual Studio (5 CVEs)
| Important severity | |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-49044 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-49050 | Visual Studio Code Python Extension Remote Code Execution Vulnerability |
| Moderate severity | |
| CVE-2024-49049 | Visual Studio Code Remote Extension Elevation of Privilege Vulnerability |
Azure (3 CVEs)
| Important severity | |
| CVE-2024-43602 | Azure CycleCloud Remote Code Execution Vulnerability |
| CVE-2024-43613 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-49042 | Azure Database for PostgreSQL Flexible Server Extension Elevation of Privilege Vulnerability |
.NET (2 CVEs)
| Important severity | |
| CVE-2024-43498 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-43499 | .NET and Visual Studio Denial of Service Vulnerability |
airlift.microsoft.com (1 CVE)
| Important severity | |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Vulnerability |
Exchange (1 CVE)
| Important severity | |
| CVE-2024-49040 | Microsoft Exchange Server Spoofing Vulnerability |
LightGBM (1 CVE)
| Important severity | |
| CVE-2024-43598 | LightGBM Remote Code Execution Vulnerability |
PC Manager (1 CVE)
| Important severity | |
| CVE-2024-49051 | Microsoft PC Manager Elevation of Privilege Vulnerability |
TorchGeo (1 CVE)
| Important severity | |
| CVE-2024-49048 | TorchGeo Remote Code Execution Vulnerability |
Word (1 CVE)
| Important severity | |
| CVE-2024-49033 | Microsoft Word Security Feature Bypass Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the November release.
| CVE-2024-5535 | Azure, CBL Mariner, Defender | OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread |
| CVE-2024-10826 | Edge | Chromium: CVE-2024-10826 Use after free in Family Experiences |
| CVE-2024-10827 | Edge | Chromium: CVE-2024-10827 Use after free in Serial |
Appendix E: Server 2025
This is a list of CVEs affecting Server 2025, which some users may have inadvertently received last week.
| CVE-2024-38203 | CVE-2024-43625 | CVE-2024-43639 |
| CVE-2024-38264 | CVE-2024-43626 | CVE-2024-43641 |
| CVE-2024-43449 | CVE-2024-43627 | CVE-2024-43642 |
| CVE-2024-43450 | CVE-2024-43628 | CVE-2024-43643 |
| CVE-2024-43451 | CVE-2024-43629 | CVE-2024-43644 |
| CVE-2024-43452 | CVE-2024-43630 | CVE-2024-43646 |
| CVE-2024-43620 | CVE-2024-43631 | CVE-2024-49019 |
| CVE-2024-43621 | CVE-2024-43635 | CVE-2024-49039 |
| CVE-2024-43622 | CVE-2024-43636 | CVE-2024-49046 |
| CVE-2024-43623 | CVE-2024-43637 | |
| CVE-2024-43624 | CVE-2024-43638 |