Authored by Aayush Tyagi
Video game hacks, cracked software, and free crypto tools remain popular bait for malware authors. Recently, McAfee Labs uncovered several GitHub repositories offering these tempting “rewards,” but a closer look reveals something more sinister. As the saying goes, if it seems too good to be true, it probably is.
GitHub is often exploited for malware distribution due to its accessibility, trustworthiness, and developer-friendly features. Attackers can easily create free accounts and host repositories that appear legitimate, leveraging GitHub’s reputation to deceive users.
McAfee Labs encountered multiple repositories, offering game hacks for top-selling video games such as Apex Legends, Minecraft, Counter Strike 2.0, Roblox, Valorant,
Fortnite, Call of Duty, GTA V and or offering cracked versions of popular software and services, such as Spotify Premium, FL Studio, Adobe Express, SketchUp Pro, Xbox Game Pass, and Discord to name a few.
Executive summary
These attack chains begin when users would search for Game Hacks, cracked software or tools related to Cryptocurrency on the internet, where they would eventually come across GitHub repositories or YouTube Videos leading to such GitHub repositories, offering such software.
We noticed a network of such repositories where the description of software keeps on changing, but the payload remains the same: a Lumma Stealer variant. Every week, a new set of repositories with a new malware variant is released, as the older repositories are detected and removed by GitHub. These repositories also include distribution licenses and software screenshots to enhance their appearance of legitimacy.
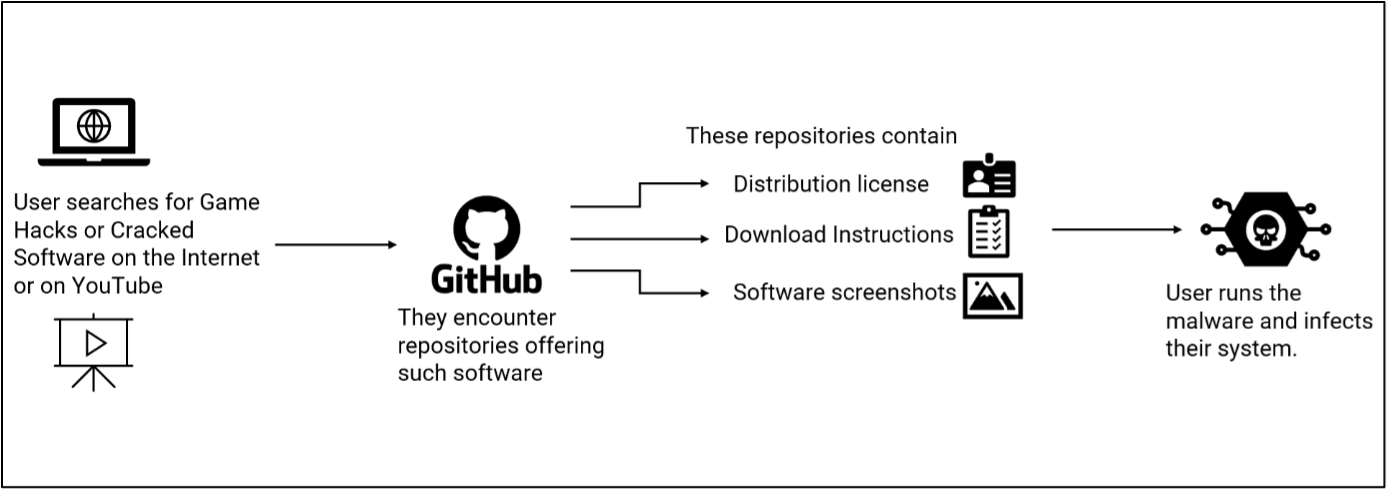
Figure 1: Attack Vector
These repositories also contain instructions on how to download and run the malware and ask the user to disable Windows Defender or any AV software, before downloading the malware. They provide the reasoning that, since the software is related to game hacks or by-passing software authentication or crypto-currency mining, AV products will detect and delete these applications.
This social engineering technique, combined with the trustworthiness of GitHub works well in the favor of malware authors, enabling them to infect more users.
Children are frequently targeted by such scams, as malware authors exploit their interest in game hacks by highlighting potential features and benefits, making it easier to infect more systems.
Technical Analysis
As discussed above, the users would come across malicious repositories through searching the internet (highlighted in red).
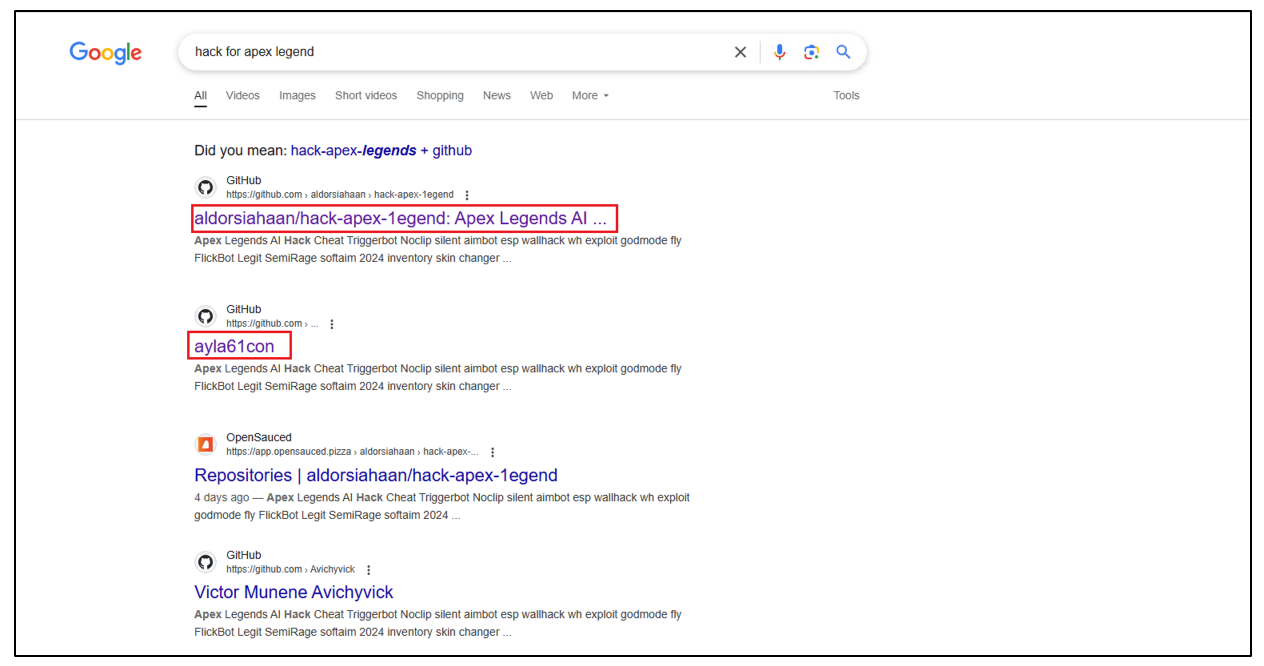
Figure 2: Internet Search showing GitHub results.
Or through YouTube videos, that contain a link to the repository in the description (highlighted in red).
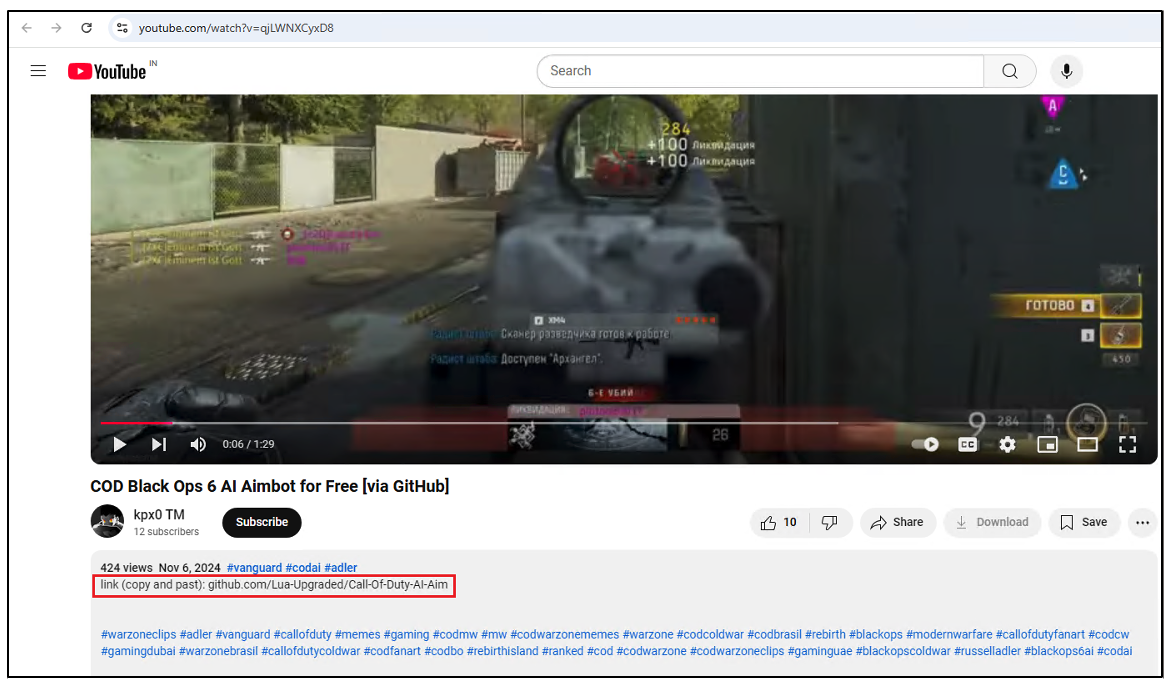
Figure 3: YouTube Video containing malicious URL in description.
Once the user accesses the GitHub repository, it contains a Distribution license and other supporting files, to trick the user into thinking that the repository is genuine and credible.
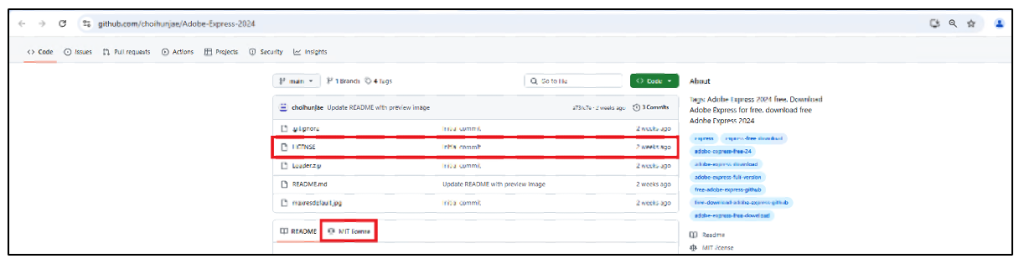
Figure 4: GitHub repository containing Distribution license.
Repositories also contain a detailed description of the software and installation process further manipulating the user.
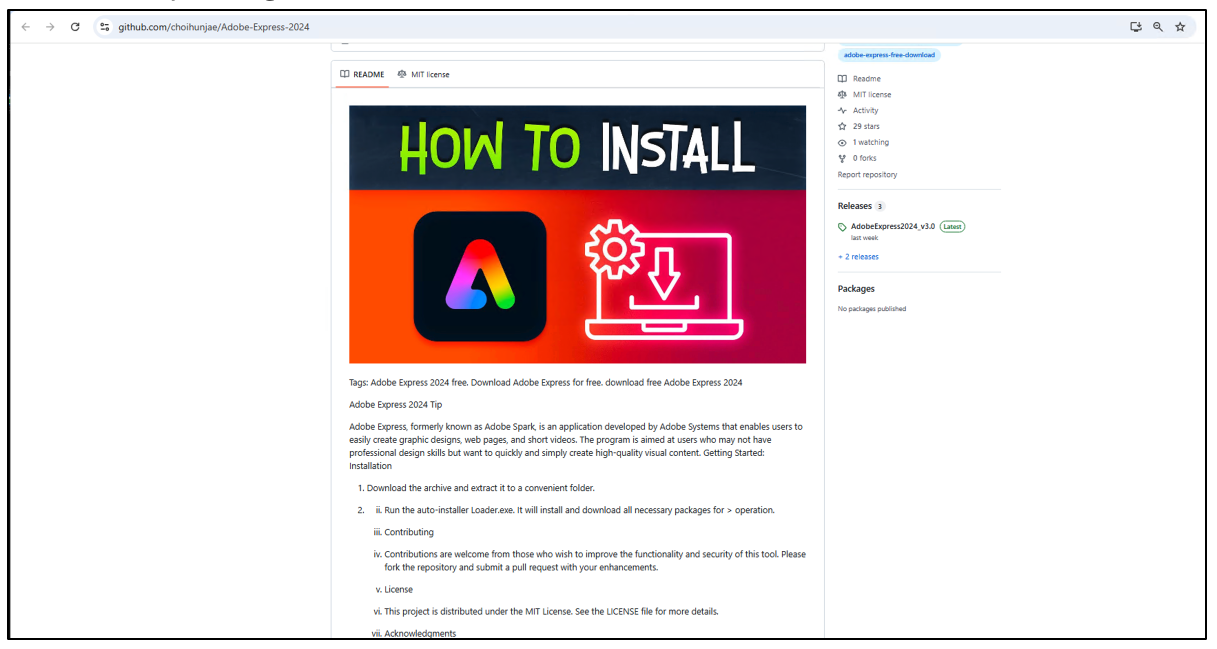
Figure 5: Download instructions present in the repository.
Sometimes, the repositories contain instructions to disable AV products, misleading users to infect themselves with the malware.
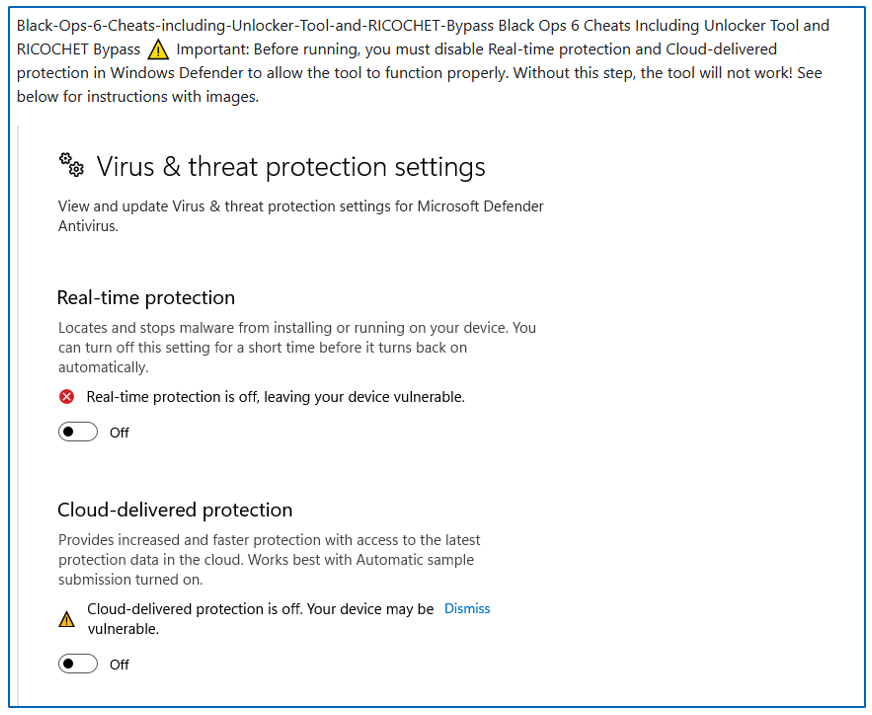
Figure 6: Instructions to disable Windows Defender.
To target more children, repositories contain a detailed description of the software; by highlighting all the features included within the package, such as Aimbots and Speed Hacks, and how easily they will be able to gain an advantage over their opponents.
They even mention that the package comes with advance Anti-Ban system, so their account won’t be suspended, and that the software has a popular community, to create a perception that, since multiple users are already using this software, it must be safe to use and that, by not using the software, they are missing out.
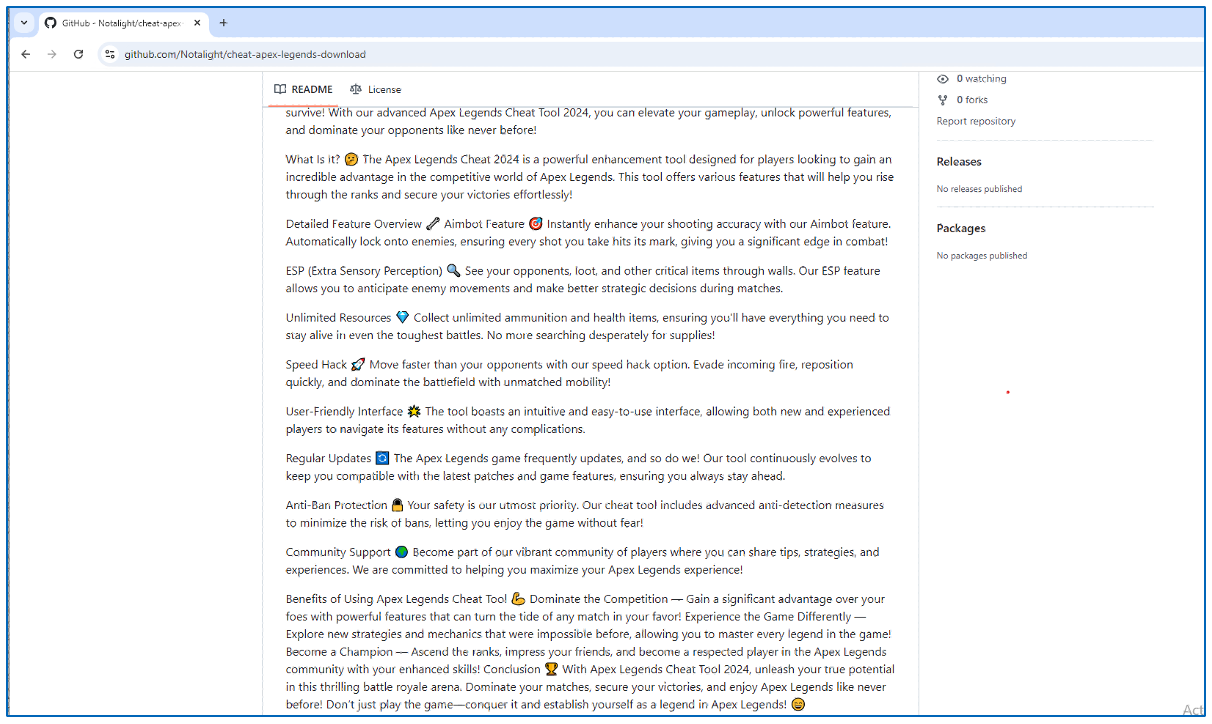
Figure 7: Features mentioned in the GitHub repository.
The downloaded files, in most cases, were Lumma Stealer variants, but observing the latest repositories, we noticed new malware variants were also being distributed through the same infection vector.
Once the user downloads the file, they get the following set of files.
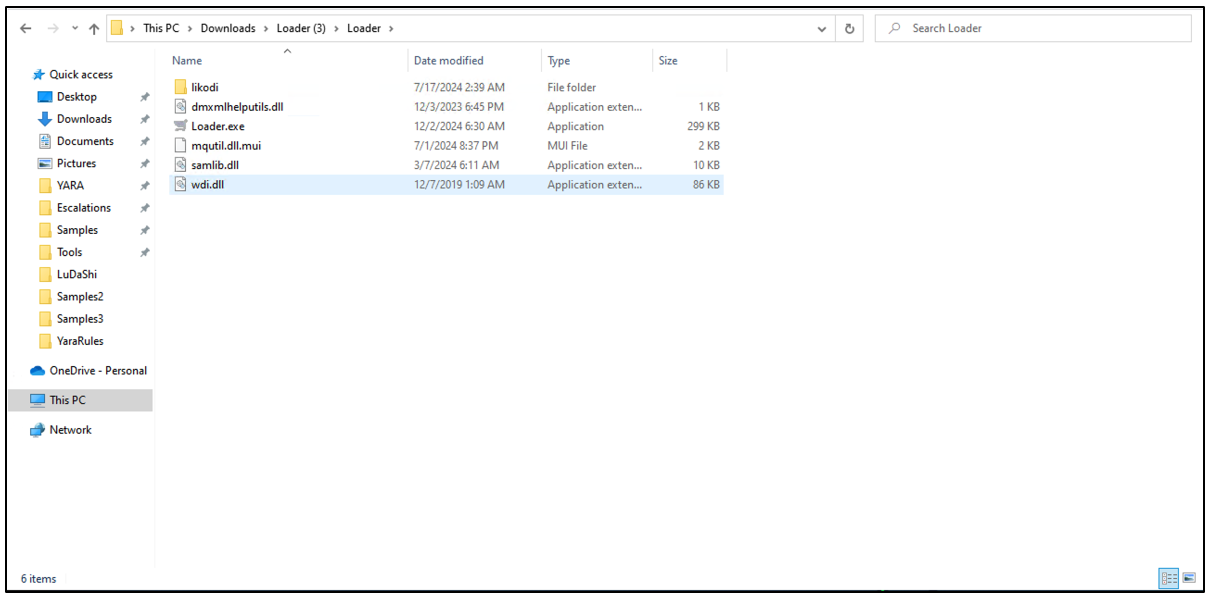
Figure 8: Files downloaded from GitHub repository.
On running the ‘Loader.exe’ file, as instructed, it iterates through the system and the registry keys to collect sensitive information.
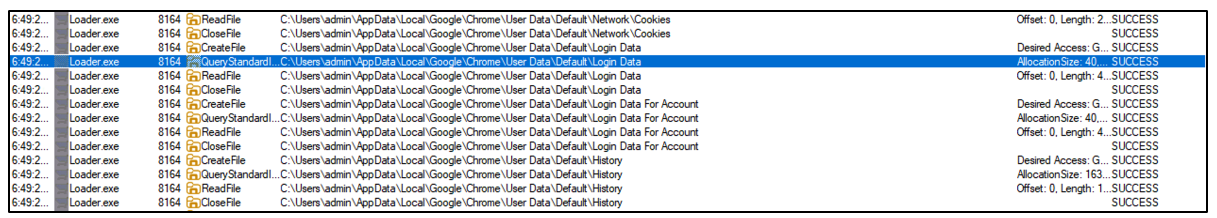
Figure 9: Loader.exe checking for Login credentials for Chrome.
It searches for crypto wallets and password related files. It searches for a list of browsers installed and iterates through user data, to gather anything useful.

Figure 10: Loader.exe checking for Browsers installed on the system.
Then the malware connects to C2 servers to transfer data.

Figure 11: Loader.exe connecting to C2 servers to transfer data.
This behavior is similar to the Lumma Stealer variants we have seen earlier.
Detection and Mitigation Strategies
McAfee blocks this infection chain at multiple stages:
- URL blocking of the GitHub repository.
Figure 12: McAfee blocking URLs
- Detecting downloaded malware.
Figure 13: McAfee blocking the malicious file
Conclusion and Recommendations
In conclusion, the GitHub repository infection chain demonstrates how cybercriminals exploit accessibility and trustworthiness of popular websites such as GitHub, to distribute malware like Lumma Stealer. By leveraging the user’s desire to use game hacks, to be better at a certain video game or obtain licensed software for free, they trick users into infecting themselves.
At McAfee Labs, we are committed to helping organizations protect themselves against sophisticated cyber threats, such as the GitHub repository technique. Here are our recommended mitigations and remediations:
- Children are usually the prime targets for such scams, it is important to educate the young ones and teach them how to avoid such fishy websites.
- Conduct regular training sessions to educate users about social engineering tactics and phishing schemes.
- Install and maintain updated antivirus and anti-malware software on all endpoints.
- Use network segmentation to limit the spread of malware within the organization.
- Ensure all operating systems, software, and applications are kept up to date with the latest security patches.
- Avoid downloading cracked software or visiting suspicious websites.
- Verify URLs in emails, especially from unknown or unexpected sources.
- Keep antivirus solutions updated and actively scanning.
- Avoid downloading Game hacks or Crypto software from unofficial websites.
- If possible, read reviews about the software you’re downloading and see what other users are saying about the malware.
- Regularly patch browsers, operating systems, and applications.
- Monitor the Temp folder for unusual or suspicious files.
Indicators of Compromise (IoCs)
As of publishing this blog, these are the GitHub repositories that are currently active.
| File Type | SHA256/URLs |
| URLs | github[.]com/632763276327ermwhatthesigma/hack-apex-1egend |
| github[.]com/VynnProjects/h4ck-f0rtnite | |
| github[.]com/TechWezTheMan/Discord-AllinOne-Tool | |
| github[.]com/UNDERBOSSDS/ESET-KeyGen-2024 | |
| github[.]com/Rinkocuh/Dayz-Cheat-H4ck-A1mb0t | |
| github[.]com/Magercat/Al-Photoshop-2024 | |
| github[.]com/nate24321/minecraft-cheat2024 | |
| github[.]com/classroom-x-games/counter-str1ke-2-h4ck | |
| github[.]com/LittleHa1r/ESET-KeyGen-2024 | |
| github[.]com/ferhatdermaster/Adobe-Express-2024 | |
| github[.]com/CrazFrogb/23fasd21/releases/download/loader/Loader[.]Github[.]zip | |
| github[.]com/flashkiller2018/Black-Ops-6-Cheats-including-Unlocker-Tool-and-RICOCHET-Bypass | |
| github[.]com/Notalight/h4ck-f0rtnite | |
| github[.]com/Ayush9876643/r0blox-synapse-x-free | |
| github[.]com/FlqmzeCraft/cheat-escape-from-tarkov | |
| github[.]com/Ayush9876643/cheat-escape-from-tarkov | |
| github[.]com/Ayush9876643/rust-hack-fr33 | |
| github[.]com/ppetriix/rust-hack-fr33 | |
| github[.]com/Ayush9876643/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/LandonPasana21/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/Ayush9876643/Rainbow-S1x-Siege-Cheat | |
| github[.]com/Ayush9876643/SonyVegas-2024 | |
| github[.]com/123456789433/SonyVegas-2024 | |
| github[.]com/Ayush9876643/Nexus-Roblox | |
| github[.]com/cIeopatra/Nexus-Roblox | |
| github[.]com/Ayush9876643/m0dmenu-gta5-free | |
| github[.]com/GerardoR17/m0dmenu-gta5-free | |
| github[.]com/Ayush9876643/minecraft-cheat2024 | |
| github[.]com/RakoBman/cheat-apex-legends-download | |
| github[.]com/Ayush9876643/cheat-apex-legends-download | |
| github[.]com/cIiqued/FL-Studio | |
| github[.]com/Ayush9876643/FL-Studio | |
| github[.]com/Axsle-gif/h4ck-f0rtnite | |
| github[.]com/Ayush9876643/h4ck-f0rtnite | |
| github[.]com/SUPAAAMAN/m0dmenu-gta5-free | |
| github[.]com/atomicthefemboy/cheat-apex-legends-download | |
| github[.]com/FlqmzeCraft/cheat-escape-from-tarkov | |
| github[.]com/Notalight/h4ck-f0rtnite | |
| github[.]com/Notalight/FL-Studio | |
| github[.]com/Notalight/r0blox-synapse-x-free | |
| github[.]com/Notalight/cheat-apex-legends-download | |
| github[.]com/Notalight/cheat-escape-from-tarkov | |
| github[.]com/Notalight/rust-hack-fr33 | |
| github[.]com/Notalight/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/Notalight/Rainbow-S1x-Siege-Cheat | |
| github[.]com/Notalight/SonyVegas-2024 | |
| github[.]com/Notalight/Nexus-Roblox | |
| github[.]com/Notalight/minecraft-cheat2024 | |
| github[.]com/Notalight/m0dmenu-gta5-free | |
| github[.]com/ZinkosBR/r0blox-synapse-x-free | |
| github[.]com/ZinkosBR/cheat-escape-from-tarkov | |
| github[.]com/ZinkosBR/rust-hack-fr33 | |
| github[.]com/ZinkosBR/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/ZinkosBR/Rainbow-S1x-Siege-Cheat | |
| github[.]com/ZinkosBR/Nexus-Roblox | |
| github[.]com/ZinkosBR/m0dmenu-gta5-free | |
| github[.]com/ZinkosBR/minecraft-cheat2024 | |
| github[.]com/ZinkosBR/h4ck-f0rtnite | |
| github[.]com/ZinkosBR/FL-Studio | |
| github[.]com/ZinkosBR/cheat-apex-legends-download | |
| github[.]com/EliminatorGithub/counter-str1ke-2-h4ck | |
| Github[.]com/ashishkumarku10/call-0f-duty-warz0ne-h4ck | |
| EXEs | CB6DDBF14DBEC8AF55986778811571E6 |
| C610FD2A7B958E79F91C5F058C7E3147 | |
| 3BBD94250371A5B8F88B969767418D70 | |
| CF19765D8A9A2C2FD11A7A8C4BA3DEDA | |
| 69E530BC331988E4E6FE904D2D23242A | |
| 35A2BDC924235B5FA131095985F796EF | |
| EB604E2A70243ACB885FE5A944A647C3 | |
| 690DBCEA5902A1613CEE46995BE65909 | |
| 2DF535AFF67A94E1CDAD169FFCC4562A | |
| 84100E7D46DF60FE33A85F16298EE41C | |
| 00BA06448D5E03DFBFA60A4BC2219193 | |
| C2 Domains | 104.21.48.1 |
| 104.21.112.1 | |
| 104.21.16.1 |



