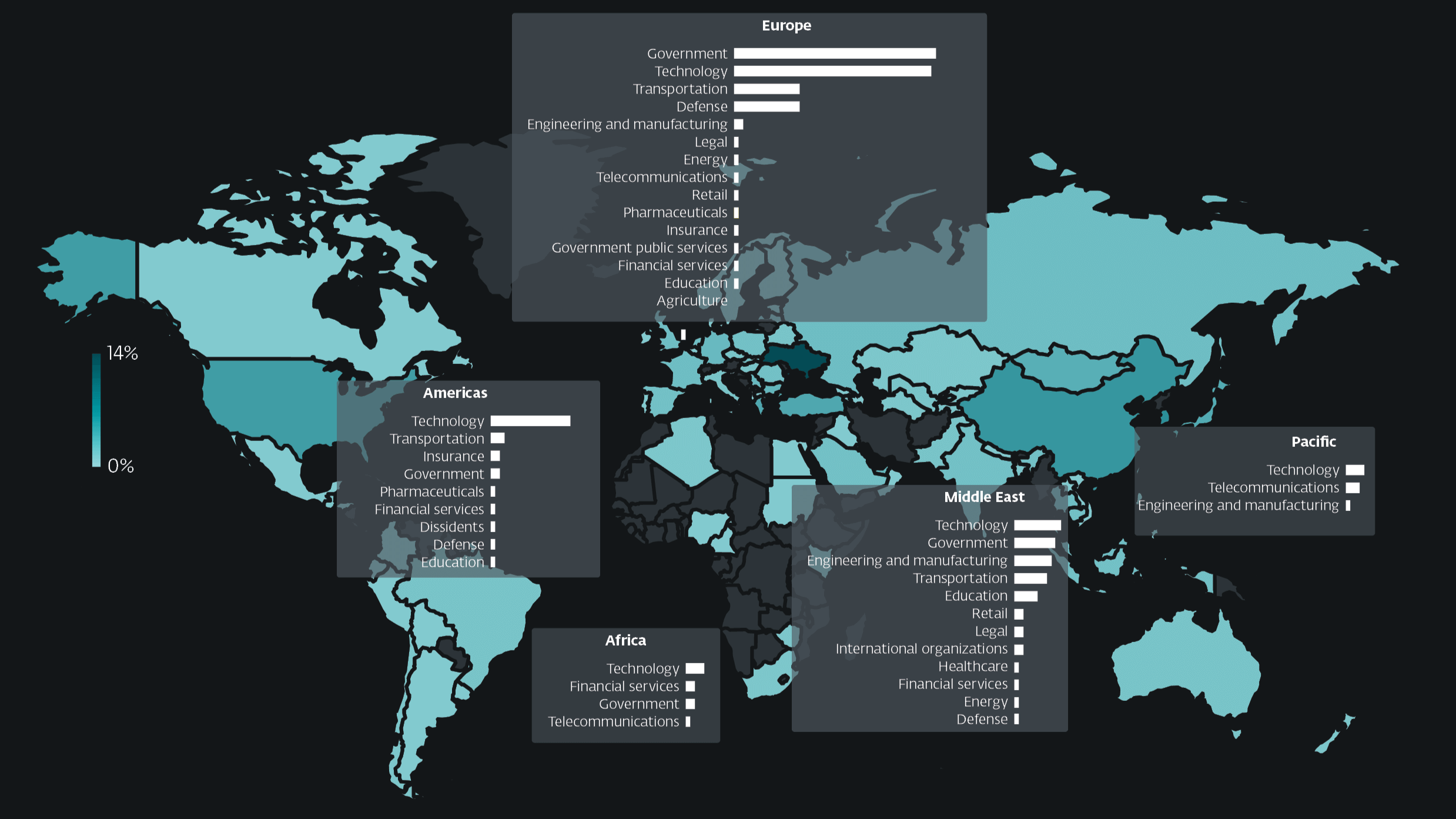
ESET APT Activity Report Q4 2024–Q1 2025 summarizes notable activities of selected advanced persistent threat (APT) groups that were documented by ESET researchers from October 2024 until the end of March 2025. The highlighted operations are representative of the broader landscape of threats we investigated during this period, illustrating the key trends and developments, and contain only a fraction of the cybersecurity intelligence data provided to customers of ESET’s private APT reports.
During the monitored period, China-aligned threat actors continued engaging in persistent espionage campaigns with a focus on European organizations. Mustang Panda remained the most active, targeting governmental institutions and maritime transportation companies via Korplug loaders and malicious USB drives. DigitalRecyclers continued targeting EU governmental entities, employing the KMA VPN anonymization network and deploying the RClient, HydroRShell, and GiftBox backdoors. PerplexedGoblin used its new espionage backdoor, which we named NanoSlate, against a Central European government entity, while Webworm targeted a Serbian government organization using SoftEther VPN, emphasizing the continued popularity of this tool among China-aligned groups. Additionally, we believe that a ShadowPad cluster that may sporadically deploy ransomware for financial gain is primarily engaged in espionage. We also highlighted Worok’s frequent use of shared espionage toolsets such as HDMan, PhantomNet, and Sonifake, addressing several inconsistent third-party attributions of campaigns involving these tools to other groups.
Iran-aligned threat actors remained highly active, led by MuddyWater, which frequently leveraged remote monitoring and management (RMM) software in spearphishing attacks. Notably, MuddyWater collaborated closely with Lyceum, an OilRig subgroup, to target an Israeli manufacturing company. BladedFeline revisited its earlier victim, a telecommunications company in Uzbekistan, coinciding with Iran’s diplomatic outreach. CyberToufan conducted destructive operations, deploying a wiper attack against multiple organizations in Israel.
North Korea-aligned threat actors were particularly active in financially motivated campaigns. DeceptiveDevelopment significantly broadened its targeting, using fake job listings primarily within the cryptocurrency, blockchain, and finance sectors. The group employed innovative social engineering techniques, such as ClickFix attacks and bogus GitHub issue posts, to distribute the multiplatform WeaselStore malware. The Bybit cryptocurrency theft, attributed by the FBI to TraderTraitor, involved a supply-chain compromise of Safe{Wallet}, that caused losses of approximately USD 1.5 billion. Meanwhile, other North Korea-aligned groups saw fluctuations in their operational tempo: In early 2025, Kimsuky and Konni returned to their usual activity levels after a noticeable decline at the end of 2024, shifting their targeting away from English-speaking think tanks, NGOs, and North Korea experts to focus primarily on South Korean entities and diplomatic personnel; and Andariel resurfaced, after a year of inactivity, with a sophisticated attack against a South Korean industrial software company.
Russia-aligned threat actors, notably Sednit and Gamaredon, maintained aggressive campaigns primarily targeting Ukraine and EU countries. Sednit refined its exploitation of cross-site scripting (XSS) vulnerabilities in webmail services, expanding Operation RoundPress from Roundcube to include Horde, MDaemon, and Zimbra. We discovered that the group successfully leveraged a zero-day vulnerability in MDaemon Email Server (CVE‑2024‑11182) against Ukrainian companies, while RomCom demonstrated advanced capabilities by deploying zero-day exploits against Mozilla Firefox (CVE‑2024‑9680) and Microsoft Windows (CVE‑2024‑49039). All of these vulnerabilities were reported by ESET researchers to respective vendors. Gamaredon remained the most prolific actor targeting Ukraine, enhancing malware obfuscation and introducing PteroBox, a file stealer leveraging Dropbox, while the infamous Sandworm group intensified destructive operations against Ukrainian energy companies, deploying a new wiper named ZEROLOT via Active Directory Group Policy and utilizing RMM tools in early compromise stages.
Finally, notable activities by lesser-known groups included APT‑C‑60 focusing on individuals in Japan who are possibly linked to North Korea, and a highly targeted phishing campaign, conducted by an as yet unidentified threat actor, impersonating the World Economic Forum and election websites, aiming to obtain sensitive information from Ukrainian officials and diplomats. In addition, StealthFalcon conducted espionage focused operations in Türkiye and Pakistan.
Malicious activities described in ESET APT Activity Report Q4 2024–Q1 2025 are detected by ESET products; shared intelligence is based mostly on proprietary ESET telemetry data and has been verified by ESET researchers.