Mishaal Rahman / Android Authority
TL;DR
- Android 15 has new restrictions on what permissions sideloaded apps can be easily granted.
- Sideloaded apps can no longer be easily granted permission to draw over the screen, obtain usage statistics, act as a device admin, and more.
- This is an expansion of the restricted settings feature introduced in Android 13, which can still be manually disabled on a per-app basis in Android 15.
For power users, there’s no question that being able to install apps from outside the Google Play Store, i.e., sideloading, is one of the biggest advantages of Android compared to iOS. Sideloading gives users the freedom to install any application they want, even if it’s not approved by Google or, more importantly, the authorities. Because distributing apps directly to users is easier than publishing them on app stores like Google Play, many hackers rely on sideloading to infect users’ devices with malware. To combat this, Google is introducing new restrictions in Android 15 that make it harder for sideloaded apps to obtain sensitive permissions.
Before I go any further, I need to address Google’s intentions with this change. Is Google restricting what permissions sideloaded apps can obtain because they actually want to protect users, or are they doing it to keep people on the Google Play Store? Given the many court cases and legal battles that Google has been caught up with in recent years, it’s easy to be skeptical that Google has good intentions with this change. However, it’s important to consider two facts.
First, sideloading is a common vector for malware due to the lower barrier of entry for distribution. Second, these restrictions don’t apply to any third-party app stores for Android that utilize the operating system’s purpose-built API for installing apps. In fact, Android 15’s restrictions on sideloaded apps are merely an expansion of a security change introduced in a previous version, a change that has not materially impacted third-party app stores and can still be manually disabled by the user.
The change I’m referring to is called restricted settings, a feature introduced in Android 13 that makes it harder for sideloaded apps to obtain certain sensitive permissions.
For the purpose of the restricted settings feature, Android considers apps to be “sideloaded” if they were installed from an app that didn’t use the purpose-built installation API designed for app stores. Typically, this includes installations from apps like web browsers, messaging apps, or file managers. If this occurs, then the sideloaded app is denied access to permissions that grant the use of Android’s accessibility and notification listener APIs, which are two of the most powerful APIs the platform offers.
These two APIs are commonly abused by malicious apps looking to control the user’s device or steal sensitive information, which is why Google sought to restrict sideloaded apps from using them.
However, apps installed using the session-based installation API are not restricted from requesting permissions to use the accessibility or notification listener APIs. This is because the session-based installation API is typically used by third-party app stores. Google designed these restrictions to not impede third-party app stores, and they also designed them so users who know what they’re doing can still get around them.
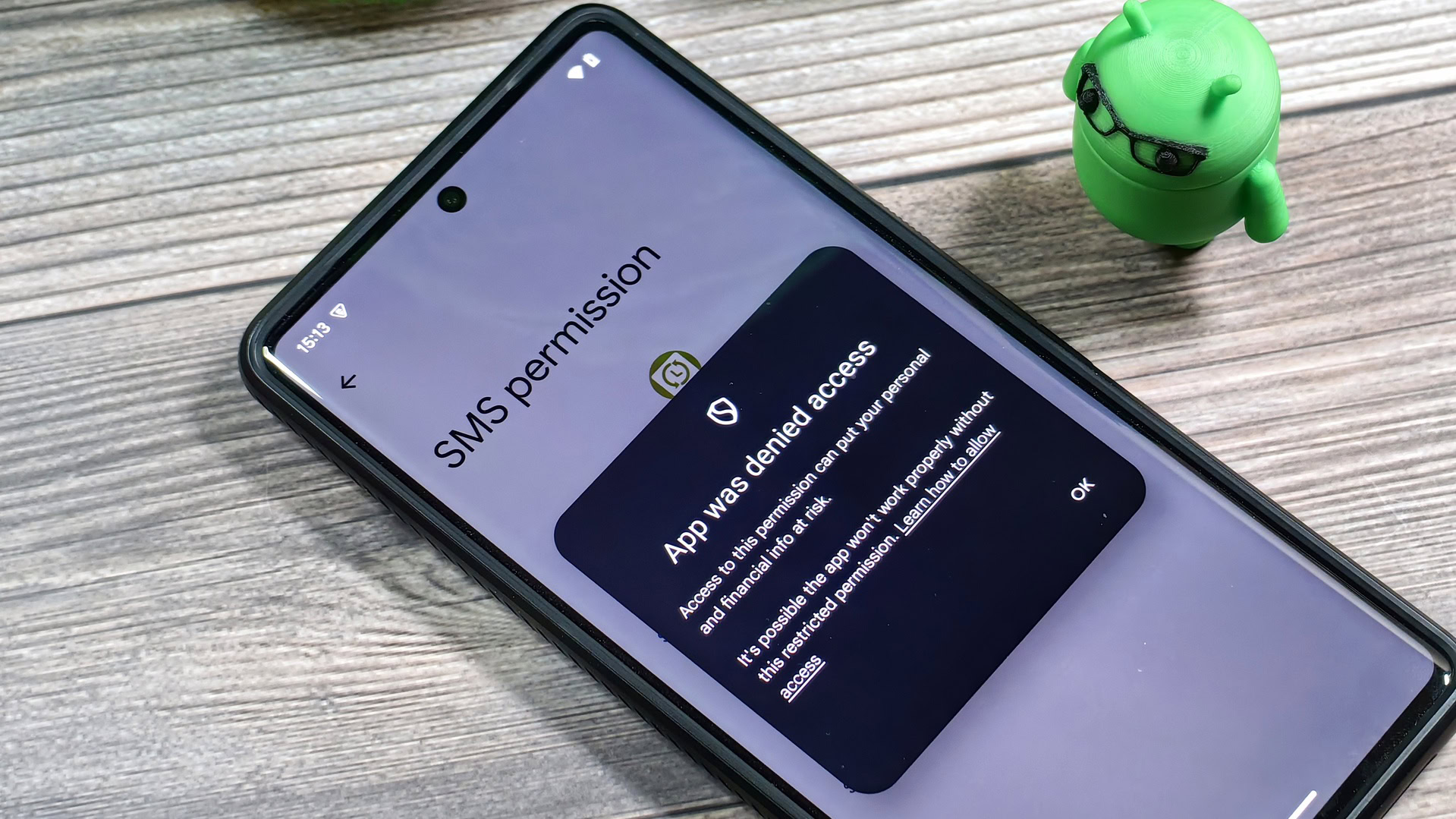
The permissions to use the accessibility and notification listener APIs aren’t the only sensitive permissions that Android has to offer, though. The SMS runtime permission lets apps read the user’s entire SMS database. The device admin permission lets apps lock or wipe the device at will. The overlay permission lets apps draw on top of other apps. The usage access permission lets apps track what apps you’re using and how often you’re using them. These permissions are all incredibly powerful, which is why the user has to manually grant them to apps.
Starting in Android 15, though, these permissions can’t be easily granted to sideloaded apps. Google is expanding the restricted settings feature to cover all the permissions I just mentioned as well as the default dialer and SMS roles. Google alluded to this expansion in a May blog post, but they only recently shared what the restrictions are in full when they published the Android 15 Compatibility Definition Document (CDD) last week.
Mishaal Rahman / Android Authority
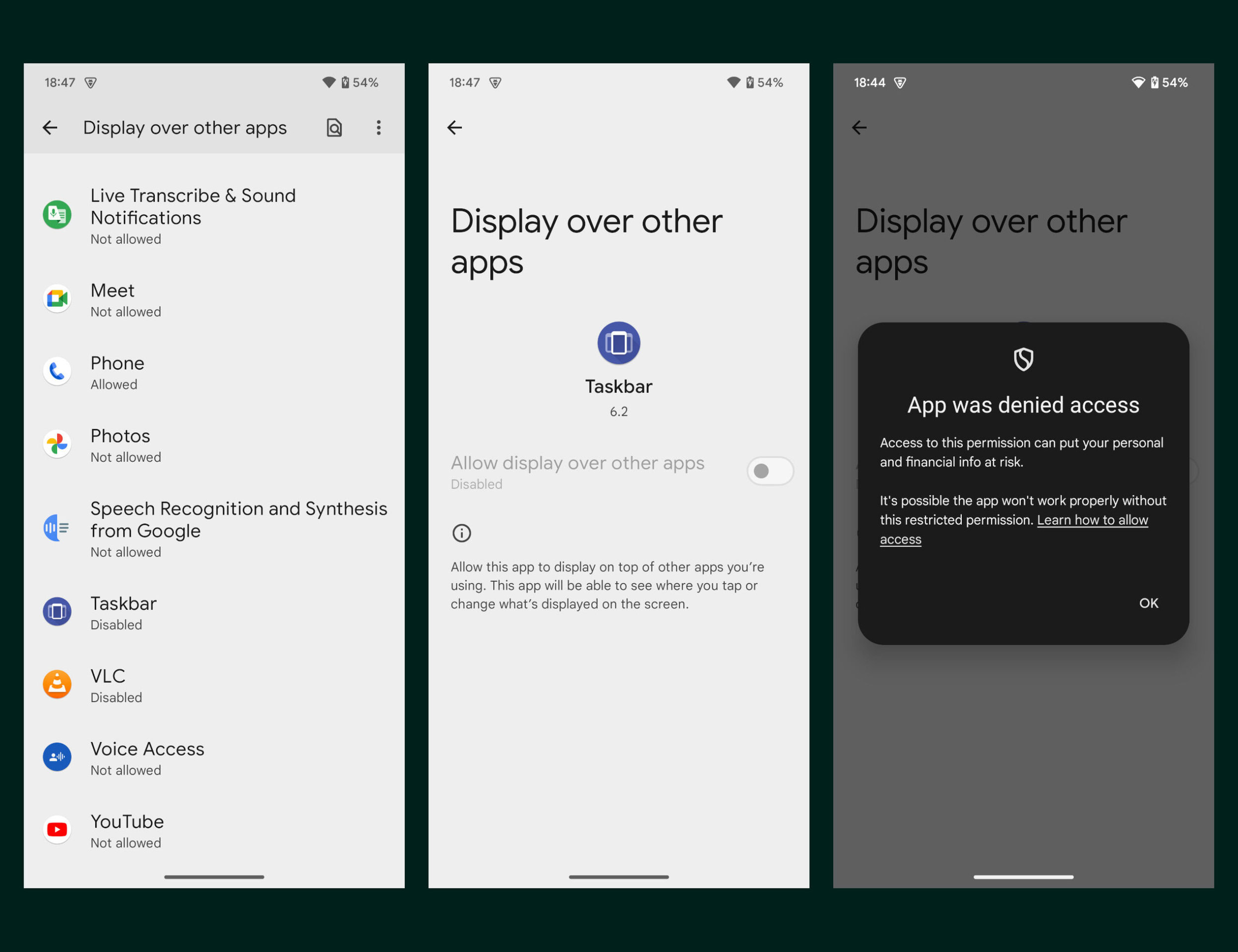
The section on restricted settings in the Android 15 CDD is quite long, but in short, Google is requiring that the following permissions and roles must have the “restricted settings” feature applied to them:
- Special permissions
- Accessibility
- Notification listener
- Device admin
- Display over other apps
- Usage access
- Roles (Default apps)
- Runtime permissions
The restricted settings feature must be applied when an app is installed “after being downloaded through an application … other than an ‘app store’ application identified by PackageManager as PACKAGE_DOWNLOADED_FILE” or when the app is installed “from a local file … identified by PackageManager as PACKAGE_SOURCE_LOCAL_FILE.”
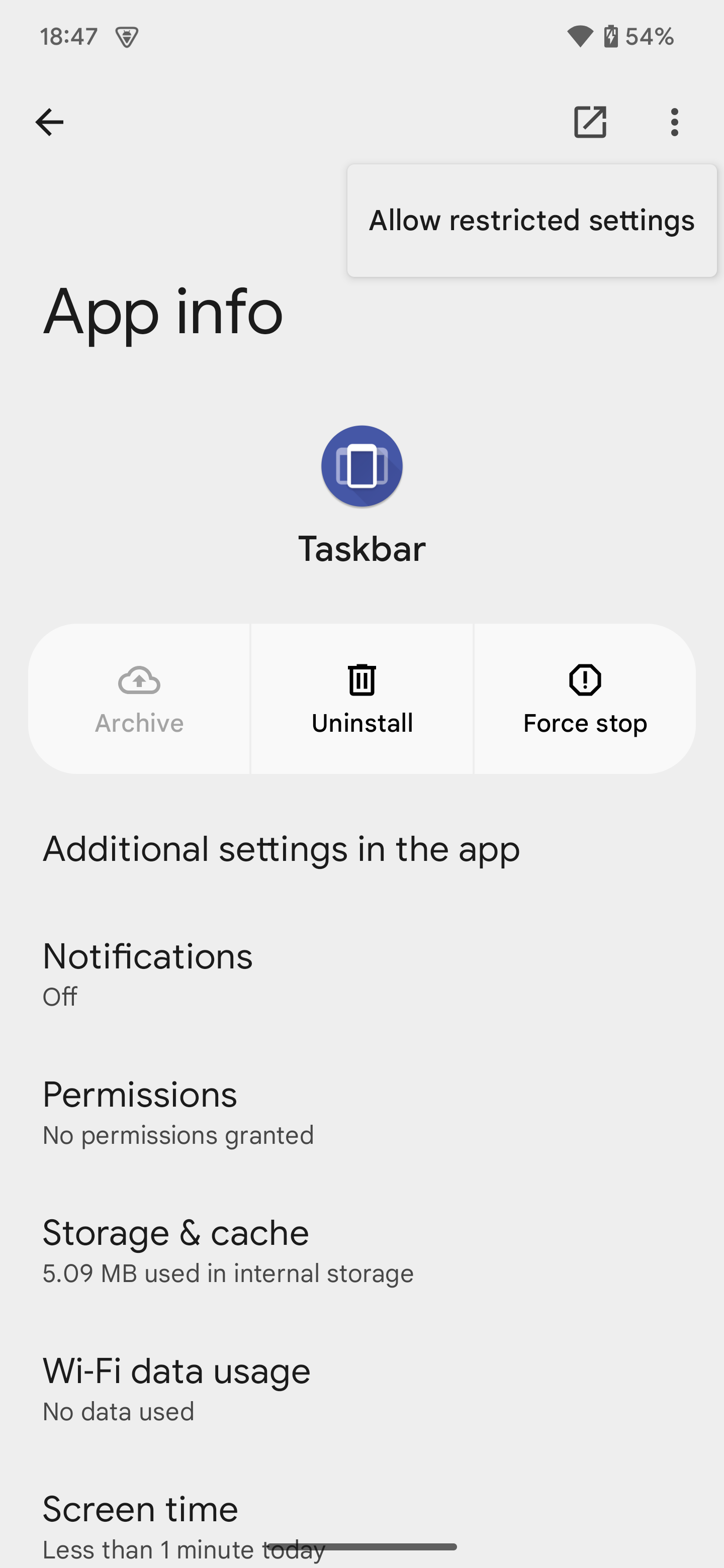
The CDD mandates that all devices running Android 15 enable restricted settings by default, but it only strongly recommends that OEMs don’t provide an option to disable restricted settings for all apps. It does, however, state that OEMs have to provide a mechanism to allow users to enable a restricted setting through the app info page, which has already been the case since Android 13.
Mishaal Rahman / Android Authority
Although the above list represents the permissions and roles that Google requires the restricted settings to apply to in Android 15, the door is left open for the restrictions to apply to more permissions in the future. In fact, Google wants OEMs to use the EnhancedConfirmationManager API to dynamically determine if other special permissions should be restricted. We talked about Android 15’s enhanced confirmation mode feature before, but it seems Google hasn’t deployed it just yet.
Google is likely to continue expanding restricted settings in future releases of Android, though we don’t know which additional permissions the feature will cover when it does.


