In today’s cybersecurity landscape, it’s not just about having robust defenses—it’s also about building trust and partnerships with the wider security community. One simple but effective way to demonstrate this openness is by implementing a security.txt file. This small addition provides a clear, standardized pathway for security researchers to report vulnerabilities, reducing friction for those who want to help protect your organization. However, only 4% of Fortune 500 companies currently use one, and that absence could be sending the wrong message.
1. A Simple Step with Direct Benefits
The value of a security.txt file is immediate and tangible. It creates a single, accessible point of contact for security researchers who may discover vulnerabilities and need to report them quickly. In a world where threats evolve constantly, the last thing you want is for helpful researchers to face hurdles in reaching your security team. This is a low-cost, high-impact way to enhance your responsiveness and streamline incident reporting.
Even if your company doesn’t have a formal bug bounty program, a security.txt file enables you to welcome and act on external security disclosures. It’s about setting the right tone and showing that your organization values security contributions from outside its walls.
2. Balancing Disclosure Rewards: When and How to Communicate
For companies that do offer rewards for disclosures, a security.txt file can serve as a transparent way to communicate program details—or signal openness to the possibility of a reward. If your bug bounty program is public, include it here to give researchers immediate clarity on how they might be compensated. But if your approach is more flexible, consider a simple statement like, “Contact for information on disclosure rewards,” which signals a willingness to discuss terms without committing to a rigid structure.
This approach lets you communicate interest without limiting options, allowing researchers to understand that their contributions are appreciated, even if a structured reward isn’t defined.
3. The Absence of Security.txt: A Missed Opportunity for Community Trust
Not having a security.txt file is more than a technical omission—it may signal a reluctance to engage with the security community. By skipping this simple step, companies can unintentionally communicate that they don’t value the efforts of ethical hackers, researchers, and white hats who could help secure their systems. In a world where collaboration is key to a resilient security posture, that’s a costly message to send.
This is especially true as your organization matures. For companies with well-developed security postures (a cumulative score of 2.0 or above on frameworks like NIST or MITRE), the lack of a security.txt file becomes harder to justify. As your security capabilities grow, consider how this minor addition can enhance your reputation and reflect a commitment to open, constructive partnerships with the community.
Conclusion: Strengthening Security Through Openness and Trust
Adopting a security.txt file isn’t just about creating a contact point; it’s a visible demonstration of your organization’s attitude toward collaborative security. When you create a clear, open channel for vulnerability reporting, you’re reinforcing a message that ethical researchers are welcome and valued. It’s an inexpensive way to foster trust, boost transparency, and align with best practices in security governance.
If your organization hasn’t yet implemented a security.txt file, consider the message this might be sending. In a time where trust is paramount, a small step like this can have outsized impact. Don’t let an oversight be mistaken for indifference—take the opportunity to signal your commitment to security and community.
Considering adding a security.txt file or want to explore more ways to strengthen your security program? Reach out—we’re here to help make security best practices accessible and actionable for your organization.
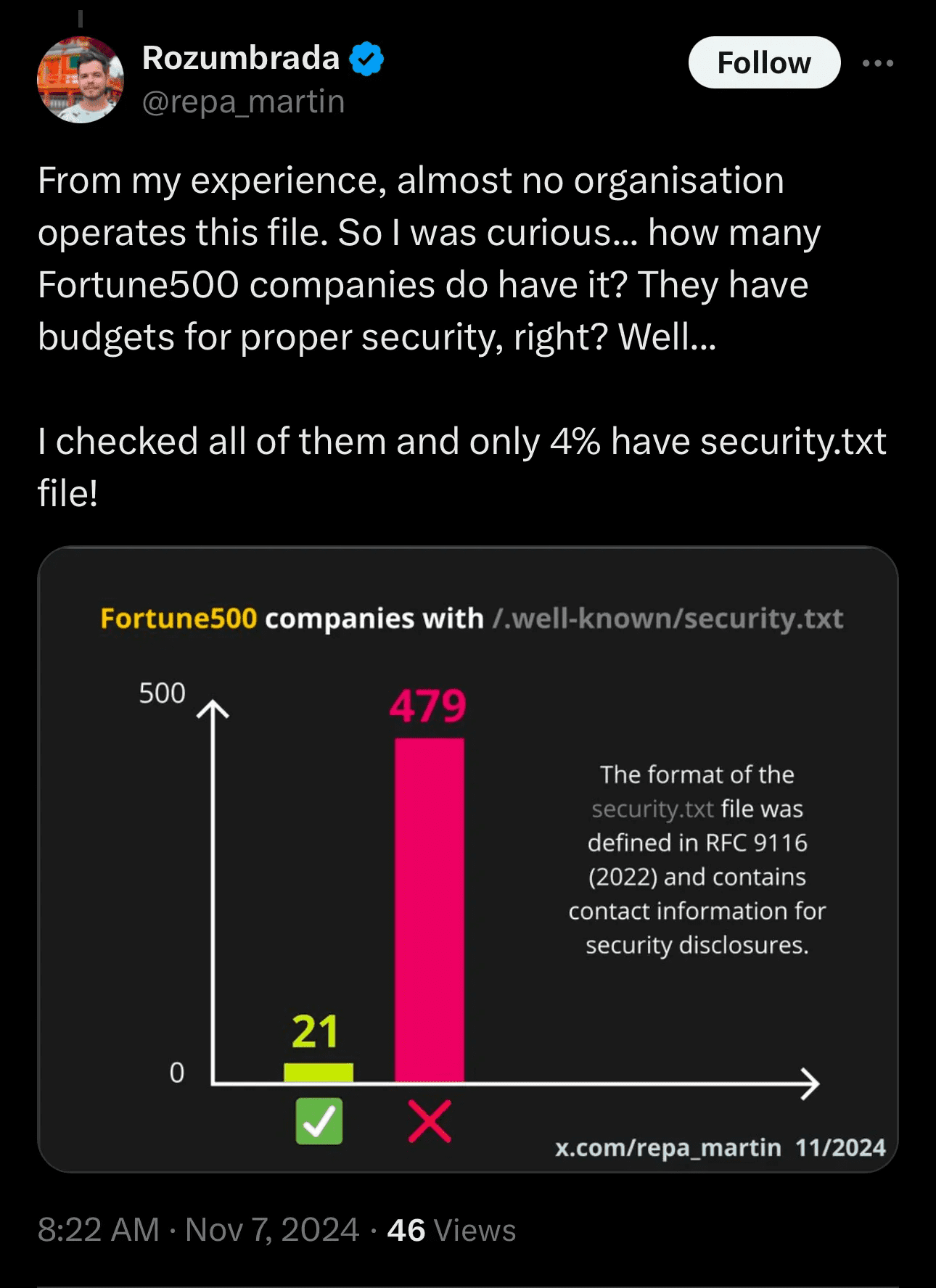
Figure 1. The Twitter Post that Inspired this Blog


